
‘Information security’ is a phrase we hear everywhere nowadays. Discussions about ‘preventing data breaches’, ‘system vulnerabilities’ or ‘user privacy’ are unavoidable when it comes to technology, and not just in countries where the EU’s General Data Protection Regulation, or similar regulations, apply. However, even with all the well-deserved attention cybersecurity is receiving, there is one specific area that most organizations forget about – printing, copying and scanning.
On this page we will cover why security is one of, if not the, most important factors when selecting a printing, copying and scanning solution for your organization. We will cover the most common security pitfalls, how to avoid them, and the certifications you can reference to make selecting the right solution for your organization easier. We will also include a short “Too Long; Didn’t Read (TL; DR)” summary of each chapter.
Here is a quick outline of the page:
Why information security is paramount
In our experience, when purchasing a document service solution, most organizations set out to buy software that is simple and user-friendly above all. But what they should be looking for is a solution which is simple and secure, and those words are equally important.
Firstly, in a broad sense, a simple solution will improve your printing security, as the better user experience will lead to fewer user errors and fewer attack surfaces. However, user-friendliness will not help against network vulnerabilities, malware, unsecure printers, or malicious actors. You need a solution which was developed with security in mind to combat these threats.
Secondly, documents often contain confidential data; passports, social security cards, pay slips, government forms, or financial statements, to name a few possibilities. Confidential data must be kept safe, but depending on your organization’s print volume, a security breach happening is a matter of when, not if, unless appropriate steps are taken to prevent it. And data breaches are expensive – they can cause your users to lose trust in you, lead to fines or potentially legal issues.
To expand on this, when we say expensive, we really mean it. According to IBM, the global average cost of a data breach in 2023 was 4.45 million USD. The report also states that (finance) companies who extensively invested in security before breaches happened saved an average of 850,000 USD. To clarify, we are not showing this to intimidate you; we just merely want to illustrate why thinking about and investing in your security and data protection before problems arise is a good idea.
Thirdly, security does not end once the document is printed or sent as a part of a scan to email service. You need to consider what you do with the data you collected, for example if the user identified themselves in some way, what will you do to keep their privacy? What will you do with the email addresses, document titles, or payment details you collected? It is important to remember that the more data you hold, the more liable you are.
Finally, risk management is also a part of a proper security setup. Questions like what your incident response plan is, how often do you make backups, how often the software is updated, what your fail-safes are so the business can continue operating, are all important to assess. Being unable to offer services because of your printing solution vendor’s poor risk management is about as frustrating as things get.
So how can you avoid these pitfalls?
Assessing your document services’ level of security can feel overwhelming, though it doesn’t have to be . Start by making sure that your network and printers are safe, e.g., check if you have any inbound ports open, if anyone can directly connect to your printer, and so forth.
Furthermore, use secure channels and maintain exemplary security hygiene for printing, copying and scanning. We will cover some of the most used printing and scanning methods and their faults in a moment, but in short, make sure that all transmissions and documents are end-to-end encrypted, and that the vendors you work with have comprehensive controls and policies in place to ensure your data isn’t mishandled or shared without your consent.
As we said above, we know this can sound intimidating and overwhelming; and there is even more to do if you want to make sure that your organization’s security is airtight. But, as demonstrated above, security is a necessary requirement when selecting a printing and payment solution for your organization.
TL; DR:
- Information security is vital for your organization.
- Information security is a broad, complex topic with many challenges.
- The more data you hold, the more liable you are.
- Start by assessing your network and hardware, then move onto your printing, copying and scanning solution.

Simplifying the process
When it comes to ensuring the security of your organization, you do not have to bear (😉) the burden alone. You can shortlist vendors and companies based on the certifications they have.
No matter which area of security you are examining, there is almost certainly a certification that covers it. With the abundance of available certifications, it is important that you look for ones that are applicable to your organization, and ones that cover multiple aspects of security. Take for example the ISO 27001 certification.
The ISO 27001 certification
Established in 2005 by the International Organization of Standardization (ISO), the ISO 27001 certification is widely recognized as “the gold standard” in information security. It outlines the prerequisites for a comprehensive Information Security Management System (ISMS) and defines how organizations should manage and handle information in a secure manner. The certification also covers the vendor’s risk management policies, incident response plans, compliance with industry-specific regulations and business continuity plan, among other things.
To become ISO certified, the vendor must undergo an independent audit by an accredited auditor. This means that the vendor’s security measures are scrutinized and evaluated by experts, providing a certain confidence in the vendor’s security claims. Furthermore, ISO certified vendors need to regularly assess their security practices, ensuring that the company is up to date about the latest vulnerabilities and practices.
Since its establishment in 2005, the certification received several major framework updates, in 2013, 2017 and in 2022. For example, the 2022 framework introduced 11 new controls, which place an emphasis on privacy and other threats that have arisen since the introduction of the 2017 framework.
Thus, we recommend that you choose a vendor that’s certified on the latest available framework (which at the time of writing is ISO 27001:2022), but a certification on an earlier framework is still immensely better than not being certified at all. That being said, every ISO 27001 certified vendor must be compliant with the 2022 framework by October 31, 2025.
There are other certifications that you could look for, for example the System and Organization Controls (SOC 2) certification, or the Cyber Essentials Certification. While selecting an ISO 27001 certified vendor is always a safe choice, consult with information security professionals to learn which certification is the best one for your organization.
In our opinion, if you are handling confidential data in any capacity, which you do when it comes to printing and payment, the ISO 27001:2022 certification is the most appropriate certification to look for.
TL; DR:
- Certifications help you identify secure vendors and solutions.
- There are many different certifications covering all aspects of security.
- The ISO 27001 certification is recognized as “the gold standard” for information security.
- Strive to choose vendors who are aligned with the most updated security frameworks.
- Consult with professionals to learn which certifications you should require from your vendors. Our recommendation is the ISO 27001:2022.
Secure scanning
Scanning is one of those services where most people do not think about the associated security risks, but upon closer examination they become quite noticeable and serious. Let’s go through some of them.
Some organizations allow their patrons to scan their documents directly onto external USB drives, or flash drives. This poses a significant security risk, as users are introducing an unknown external device to your system. This simple connection can enable malicious actors to wreak havoc on your setup, for example via keylogging software, which can threaten your whole organization and your other users.
Many organizations also offer ‘scan to email’ services. There are two major factors you must consider when using this option. Firstly, sending documents by attaching them directly to an email is absolutely not secure. If you are going to email documents to your users, you should encrypt the documents. You could then, for example, store the encrypted documents in a temporary online storage and include a link to this storage in the email you send to your users. Naturally, as emails are not safe, you should protect this link in some way, e.g., with a complex password that has a short retention period.
Secondly, to send an email to your users, you must collect their email address, either by them identifying themselves as a registered user or by asking them to fill in their email address as part of the scanning process. This brings user errors into the picture, which can result in users sending their documents to the wrong email address and thus unwillingly sharing confidential data with someone.
Thirdly, you do not want to hold on to your users’ email addresses nor their logged sessions – however, do note that certain industries, like banks, are required by law to keep this data, so please read the relevant legislation for your organization. Assuming you are not required to keep the data, you want to make sure that it is wiped from your system, preferably automatically. Remember, the more data you hold, the more liable you are.
To reiterate, the problem is not collecting the data; the problem is holding on to the collected data.
TL; DR:
- Allowing users to connect external flash drives for scanning their documents is not secure.
- Emails are not a secure method of sending scanned documents to your users, thus documents should never be directly attached to an email.
- It carries a lower risk to store scanned documents in an encrypted temporary cloud storage and email a password protected link to this storage to your users.
- Unless you work in specific industries, you should delete any data you collect on your users as soon as possible, whether that is their session logs or email addresses.
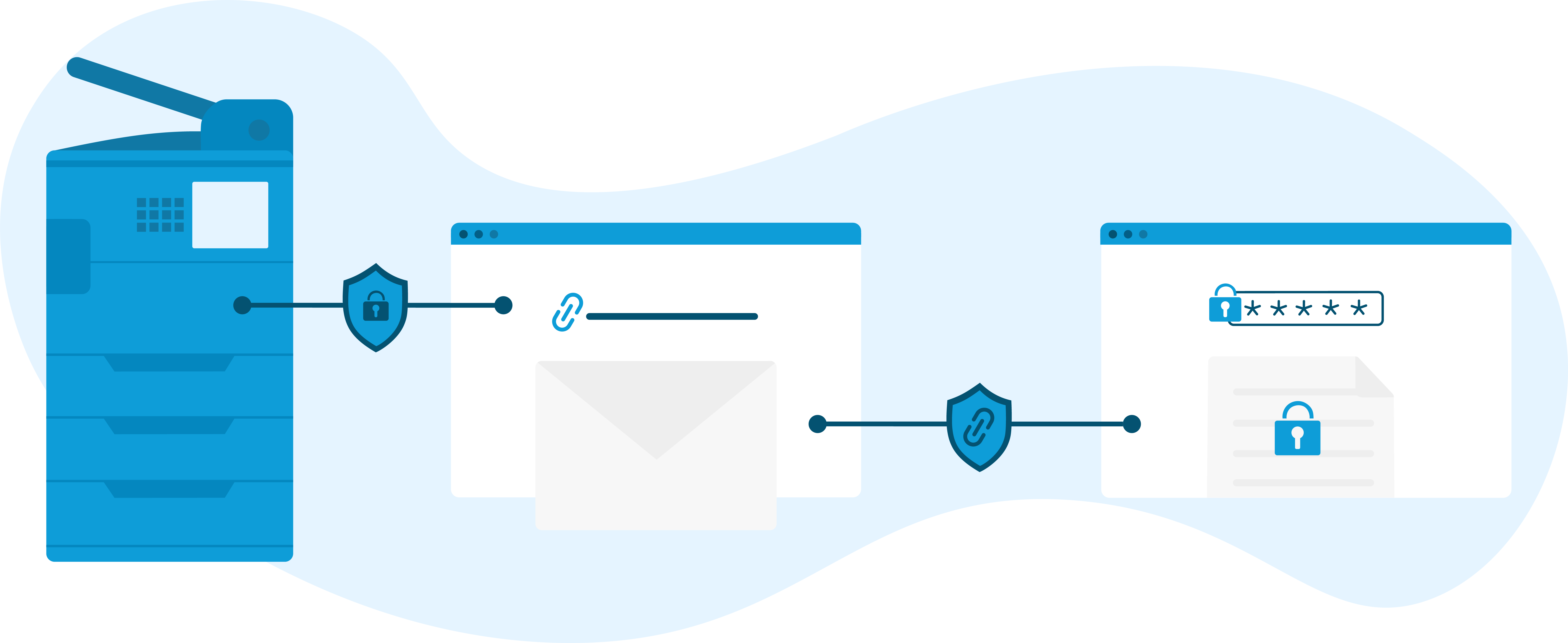
Secure printing
A very common method to offer public printing services is by asking users to email their documents to staff so they can print them out. While this is a cheap and simple way to offer printing, it is also, plainly speaking, the least secure way to do so for multiple reasons.
As we just discussed in the Secure Scanning section, sending documents via email is not secure. Additionally, by emailing staff, your users are providing you with their email addresses, which, as mentioned, you likely do not want to keep.
Furthermore, users may put the incorrect email address when sending their documents, which might lead to them emailing confidential information to malicious actors. While this last point is technically the result of a user error and hence not strictly the responsibility of your organization, we highly recommend choosing a simple solution where the possibility of errors like this is minimized.
Similarly, you do not want to keep the documents users send you either. And finally, staff having access to the users’ documents is considered unsafe from a privacy and security point of view.
To put it into broader terms, the main problems with this printing method are the lack of proper data protection, data privacy, and, to some extent, network security measures. But now that we have pointed out the most common printing related security breaches, let’s discuss what you should look for in a printing solution.
First and foremost, all documents and transmissions need to be encrypted. There is no wiggle room here: if a solution doesn’t securely encrypt your users’ documents, you should not purchase it. However, not all encryptions are equal. Think of encryption as a password to the document – the more you use this password, the more likely your account will be hacked. That is why legacy printing methods, like ‘follow-me printing’, are not as secure as they could be. Since you can print your document from any printer, every printer must have the “password” to your document, thereby making it more vulnerable.
Ideally, the decryption key (“password”) is only known by the printer you are going to use to print your document. This means that, yes, you should sacrifice a little bit of convenience and flexibility to make your printing services more secure. That said, in our experience, when using a public printer, most people already know which printer they are going to use prior to printing.
An overlooked, but nevertheless important, aspect of security is software updates. Software should always be updated to cover new vulnerabilities, or to align with updated frameworks. Many vendors charge extra for their software updates, making their software’s security levels plummet over time, unless you keep purchasing these updates.
Documents should also be kept private. This means that neither you nor your vendor’s staff should be able to access the content of any print job. Furthermore, the printing solution provider should have policies in place to prevent the mishandling or nonconsensual sharing of data.
Finally, no matter how secure the software is, it can easily fall victim to unsecure hardware and networks. Some of this responsibility is on the printing solution provider; they must use secure connections and protocols to prevent the interception of documents. The rest, however, is up to you; you need to make sure that your printers cannot be tempered by unauthorized personnel, and that unauthorized personnel cannot retrieve documents that are not theirs.
TL; DR:
- When choosing a printing solution, consider the following questions:
- How is the data protected?
- Does the solution use secure network connections and protocols?
- Is my printer secure?
- How is the users’ privacy ensured?
- Will the solution be kept up to date to cover vulnerabilities, and does updating the solution incur additional costs?
- Any printing solution that does not encrypt your users’ documents is a solution not worth purchasing
- Patrons emailing their documents to staff to print them out is one of, if not the, least secure ways to offer printing services
Secure and Simple Printing, Copying and Scanning – Princh
Princh is the standard for printing, copying, scanning and payment in public spaces. Our user-friendly cloud-based solution is built with a ‘simplicity and security first’ mindset. We allow your users to print from their own devices or public PCs, as well as to conveniently copy or scan their documents, all while offering market leading security.
Additionally, all Princh products come with integrated electronic payment, allowing your users to securely pay for their print and copy jobs via bank cards, Apple Pay and Google Pay. And since payment is truly integrated, you do not have to set up any payment agreements or invest in POS hardware.
To prove our commitment to security and privacy, Princh:
- Is the first software company in the printing and payment industry to achieve the ISO 27001:2022 certification.
- Encrypts all transmissions and documents both in-transit and rest, applying leading edge cryptography strategies, drastically reducing the chances of being hacked.
- Only stores the secret decryption keys to documents on the local printer server. This means that neither Princh nor any third party will be able to decrypt your users’ data.
- Automatically deletes all email addresses that it collects during the scanning process.
- Does not directly attach scanned files to the emails. Instead, we send users a password protected link to their documents.
- Automatically deletes all documents from the system after 24 hours.
- Has chosen a payment provider that’s PCI compliant on the highest possible level (level 1).
For further information on our products, pricing or why we are the industry leader in security, you can reach out to us here.
You can learn more about our products via our on-demand demos or read our technical requirements by clicking the buttons below to learn more about our solution.
Stay safe, and remember – the more data you hold, the more liable you are.
